|
|
| Point
Lock Frequent Ask Questions: |
|
| |
|
|
| |
|
1.
What is Point Lock? |
| |
|
2.
What security features does Point Lock provide? |
| |
|
3.
What other features does Point Lock have? |
| |
|
4,
Can Point Lock protect confidential information I access
through my company's local area network? |
| |
|
5.
What are the system requirements to run Point Lock on my
system? |
| |
|
6.
How does Point Lock provide protection? |
| |
|
7.
Does Point Lock encrypt data? |
| |
|
8.
How do I install Point Lock? |
| |
|
9.
How do I use Point Lock? |
| |
|
10.
Can't seem to find Point Lock in the Program Folders, did
the program install correctly? |
| |
|
11.
What does Folder Lock do? |
| |
|
12.
What is Hidden/Read Only function? |
| |
|
13.
How do I uninstall Point Lock? |
| |
|
14.
Are there any known programs or applications that Point Lock
is not compatible with? |
| |
|
15.
Are there any particular rules or conditions I need to
follow in setting up User Name and Password? |
| |
|
16.
What do I do if I forget my User Name or Password? |
| |
|
17.
Who will benefit from using Point Lock? |
| |
|
18.
Why can't I find Point Lock at retail stores? |
| |
|
|
| |
 1. What is Point Lock? 1. What is Point Lock?
|
| |
|
Point
Lock is a user-friendly security program that protects files
and data on personal computer systems from intruders at
keyboard level and hidden dangers that is inherent to being
connected on a network. Whether it is online peepers or
unauthorized access within your local network, you can be
assured that your data is protected with Point Lock. |
 |
| |
|
|
| |
 2. What security features does Point
Lock provide? 2. What security features does Point
Lock provide?
|
| |
|
Point Lock has many features to ensure that your data
remains private and protected from unauthorized users. It
uses 128-bit encryption for password protection, so no one
else but the authorized user can access the program. The
main protection for your data is provided by the unique
Locking functions, which prevent hackers or internal
intruders from finding and/or removing important data
while you are away from your computer, by making the
selected folders or drives disappear from your computer.
The lock features for devices such as FDD, CD-ROM, CD-R/RW,
zip Drives protects data from being copied or removed from
your computer by unauthorized users and also stops
unauthorized users from installing or writing any
malicious data to your system.
|
 |
| |
|
|
| |
 3. What other features does Point Lock
have? 3. What other features does Point Lock
have?
|
| |
|
Point
Lock has many other useful safety features such as allowing
one convenient step to clear recently used documents and
browsed sites automatically when you close the program that
prevents unauthorized users from retracing any of your
activities during your workday. Also, Point Lock does not
show in the Program tab in the Windows Start Menu so it is
not obvious to others that a security program is operating
on your computer. Another built-in safety feature is that
Point Lock can only be uninstalled by the original installer
of the program, which prevents unauthorized users from
gaining access to confidential information by deleting the
program.
|
 |
| |
|
|
| |
 4. Can Point Lock protect confidential
information I access through my company's local area
network? 4. Can Point Lock protect confidential
information I access through my company's local area
network?
|
| |
|
Yes,
by using the Network Lock feature, you can prohibit
unauthorized users from accessing confidential information
on servers or other computers on your network for malicious
intent.
|
 |
| |
|
|
| |
 5. What are the system requirements
to run Point Lock on my computer?
|
| |
|
You
will need to have a Pentium-rated CPU, at least 16MB of
memory, minimum of 5MB of free space on the hard drive, and
one of MS Windows 95/98/ME/2000/NT4.0 operating systems.
|
 |
| |
|
|
|
| |
 6.
How does Point Lock provide protection? 6.
How does Point Lock provide protection?
|
| |
|
Point
Lock takes a unique approach in data protection compared to
other security programs. It uses a patent pending technology
to hide any traces of the folder containing personal or
critical data from the system. When the program is
operating, no one but the user knows that there are
important data on the system. This approach removes any
curiosity factor that other security programs leave
unresolved. There is no other means of protection that is
safer than Point Lock since unauthorized users will not even
know that there is any valuable information on your system.
|
 |
| |
|
|
|
| |
 7.
Does Point Lock encrypt data? 7.
Does Point Lock encrypt data?
|
| |
|
Unlike
most security programs, Point Lock does not encrypt the data
it's protecting. After years of development, we have
determined that encryption is an inefficient way to protect
data. When you encrypt, it changes the data in such a way
that it cannot be displayed properly without a key. To do
this, it takes up unnecessary resources and time. Point Lock
works more efficiently, by removing all traces of your files
when in operation, instead of changing the data that could
result in permanent loss of the data.
|
 |
| |
|
| |
 8. How do I install Point Lock?
|
| |
|
Installing
Point Lock is very simple once you download the program from
one of many download sites available online. With the
install option on many of the unzip utilities currently
available, the program will launch into the setup screen as
soon as unzipped. Then, follow the directions and enter your
user name and password to complete setup. MAKE SURE YOU
REMEMBER THE USER NAME AND PASSWORD YOU USE TO INSTALL THE
PROGRAM BECAUSE YOU WILL NEED THIS INFORMATION WHEN YOU NEED
TO UNINSTALL THE PROGRAM FOR ANY REASON.
|
 |
| |
|
|
|
| |
 9. How do I use Point Lock?
|
| |
|
When
you install Point Lock, the program will create a shortcut
in the Quick Launch bar and an icon in the Control Panel
folder. You can use either of them to launch the Login
screen to run the program. Occasionally, you may change your
user name and password for security purposes, but this will
not change the original user name and password you will need
to uninstall the program.
|
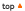 |
| |
|
|
|
| |
 10. Can't seem to find Point Lock in
the Program Folders, did the program install correctly?
|
| |
|
If
you have followed the directions during the setup, the
program will have created a shortcut in the Quick Launch bar
and in the Control Panel. As a safety feature, the program
does not show up in the Program Folders, it's a stealth
feature, so it won't be so obvious to unauthorized users
that a security program is operating on the computer.
|
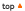 |
| |
|
|
|
| |
 11.
What does Folder Lock do? 11.
What does Folder Lock do?
|
| |
|
Once
you lock the selected folders for the Folder Lock function,
Point Lock hides the existence of the folders from
unauthorized users and even the system is unaware that there
is such a folder when the program is in operation, so you
don't have to worry even you are away form your computer. To
access those folders again, simply login to Point Lock and
the selected folders will appear in the Point Lock Full
Screen.
|
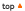 |
| |
|
| |
 12. What is Hidden/Read Only
function?
|
| |
|
This
function is different from other Windows applications with
Read Only features. With typical applications, documents are
available for all users but limiting modification rights,
but with Point Lock only AUTHORIZED users are allowed to
read the documents by searching for the specific file in the
Windows Search/Find menu.
|
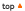 |
| |
|
|
|
| |
 13. How do I uninstall Point Lock?
|
| |
|
In
order to uninstall Point Lock program, you need to enter the
User ID and Password used to initially install the program.
You are required to enter ID and Password twice when you
first install and use the program (once when you first
install the program, and once again when you first use the
program). YOU MUST REMEMBER AND ENTER THE FIRST USER NAME
AND PASSWORD USED TO INSTALL THE PROGRAM IN ORDER TO
UNINSTALL THE PROGRAM.
|
 |
| |
|
|
|
| |
 14. Are there any known programs or
applications that Point Lock is not compatible with?
|
| |
|
Point
Lock works with all Windows based programs and applications.
Only programs you may need to watch out for are antivirus
software, during the installation process. Normally, when
you install new software we suggest that the antivirus
program be disabled after making sure that the new software
is free of virus.
|
 |
| |
|
|
|
| |
 15. Are there any particular rules
or conditions I need to follow in setting up User ID and
Password?
|
| |
|
Make
sure you choose your User ID and Password that will not be
easily guessed by others. Avoid using familiar names, birth
dates, anniversaries, and such for your password. The User
ID must be between 4 to 20 characters with no spaces in
between and the password must be 4 to 10 characters with no
spaces. Please be aware that the User ID and Password are
case sensitive.
|
 |
| |
|
|
|
| |
 16. What do I do if I forget my User
Name or Password?
|
| |
|
Should
you at any time forget your user name or password, you need
to contact us before you try uninstalling or make any
modifications to the program. Once we are able to confirm
that the user is the owner of the program, we will create a
program that will reset the User Name and Password for the
authorized owner. The process will take about 48 hours to
verify the owner information. Please be patient with us
during this process, since this program is a security
product, we need to ensure that only the authorized user
will get the program.
|
 |
| |
|
|
|
| |
 17. Who will benefit from using
Point Lock?
|
| |
|
Anybody
who works with sensitive or confidential information on the
computer will benefit with Point Lock because it will give
him or her peace of mind that the information will not be
available to any unauthorized persons. Professionals like
lawyers, engineers, accountants, executives, and such will
be able to keep confidential information, trade secrets, and
personal files from being leaked to competitors or someone
with malicious intent.
|
 |
| |
|
|
|
| |
 18. Why can't I find Point Lock at
retail stores?
|
| |
|
To
keep the cost of our products as low as possible for our
customers, we have decided to market our products in the
most cost efficient way available through online
distribution. By saving the cost of packaging, we are able
to pass on the savings, to make it easier for our customers
to make the decision of buying and benefiting from our
products. The efficient process of online distribution will
allow our customers the same satisfaction of owning and
keeping a licensed copy of our software without the worries
of misplacing or losing a physical copy of it.
|
 |


